Goon Phishing
Today the media (well some of it at least) has a story about a phishing email doing the rounds purporting to be from an Irish public sector body.
These are not really newsworthy as they happen so often, but it is important for people to be aware of the issues and risks and what to do. This because Phishing presents a significant threat to Data Protection and Information Security as it tries to get around the controls, awareness, and checkpoints that organisations will have put in place as part of their data governance for data protection.
- Phishing sent to people in a company can expose passwords and information that can let attackers get into the IT systems of the organisation. That is how Sony got hacked recently.
- Phishing sent to people in a personal capacity can expose bank details, credit card numbers, personal data (address, date of birth, family pet’s name), and even login details for services that might hold even more personal data (for example a social media account).
There is a limit to what organisations can do to protect people and their data from these kinds of email. That’s why criminals use this approach. Therefore people need to take steps to protect themselves.
This starts with awareness.
The general format and character of the email is usually along these lines:
- A plausible looking email that copies the “look and feel” of an organisation you may or may not have had dealings with arrives in your inbox
- It contains either an OFFER for something or a WARNING about something. So you might be told you’ve been selected to win a new smartphone or other object of desire, or they might tell you that they’ve lost all your data or that your account with them will be locked out if you don’t IMMEDIATELY click on a link and hand over some data to “verify” your identity.
- Sometimes they are in the language (or supposed language) of the targetted country.
DON’T CLICK THAT LINK.
HTML email, and spoofed email addresses, make it easy for a scammer to get you to drop your guard if you are not careful. Just like, in the old days, a slightly shabby suit and a dog eared identity card might have got the dodgy conman into your home, a familiar logo, a familiar sounding email address and an appeal to either your greed (“You may have won €10000!”) or fear (“We will suspend your bank account if you don’t do this!”) is the “foot in the door” for the online confidence trickster (aka “scumbag”).
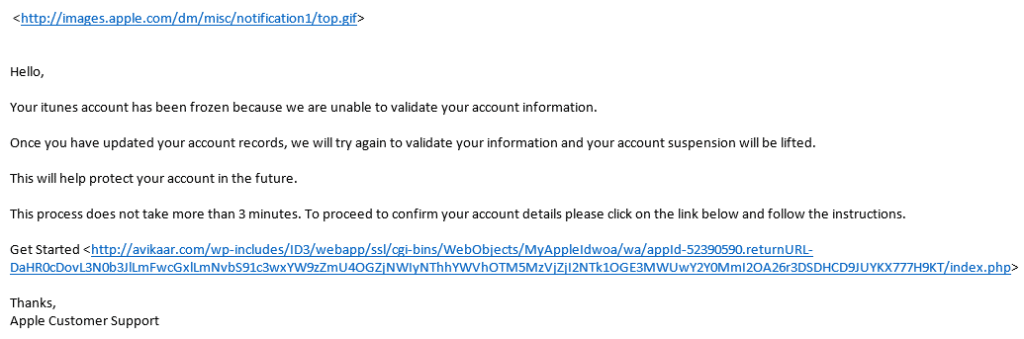
When read with the HTML features turned off, a phishing email reveals its true colours. The example below is one I received from “Apple”.
Things to note:
- The images are sourced from the Apple website. OK. That seems legit.
- The link however is to a landing page that has been hosted instide someone elses’ WordPress site (wordpress runs over 20% of the sites on the internet these days, but is a bugger to keep secure if you don’t know what you are doing). This means that the website in question (usually a small business website) has been hacked, or simply left unsecure, and nasties have been uploaded.
Clicking on the link in the email, which would look like a perfectly legitimate link to, in this case, the Apple website, would take you to a page that asks for personal data, bank account details, credit card details etc.
What can you do?
Simply: Distrust and Verify. It it looks too good or too scary it probably is. Also, these phishing emails are often written incredibly badly with. Sentences that look, like this.
The simplest things you can do:
- Is this being received to an email address you have given to this organisation. If not… FLAG AS JUNK and DELETE. (we get a few dozen everyday to the public facing email addresses for the company).
- Is this an organisation you have EVER dealt with before? If no… FLAG AS JUNK and DELETE. (I get emails from US banks and from Irish banks that I’ve never had accounts with warning me that my account will be suspended…. lol)
If it is an organisation you have dealt with in the past, and it is an email address that you would have used with them, you can still do something very simple to protect yourself and your data:
Don’t, what ever you do, Click that Link!!!
You can verify the truth of the email by going to the organisation’s website in your web browser (typing the URL for the organisation (“www.apple.com“) or, if the email has a “www.XYZ.blah/trust-us-not-evil-we-swear” link you can see in the email, type that).
- If you’ve won a prize, if you login to the site they will probably have a message for you there, or if there is a special promotion going on you will see a banner ad about it or some other information.
- If there has been a loss of data or your account is going to be suspended, there will be a NOTIFICATION of that to you as a customer.
One really basic check you can do is to make sure that ANY site you are visiting that asks you to type ANY personal data into it is secured using SSL (secure sockets layer). This costs relative buttons for organisations to put in place and there is simply no excuse for websites that have sign-in forms, contact forms, email list sign-up forms, etc. to not have it in place. Sites that are using SSL will have a green padlock icon in the address bar when you visit them.
We have worked with clients who were audited by the DPC. A specific audit check that was performed in each case was to verify that any forms that were capturing personal data were SSL protected. It was made explictly clear that this was a minimum standard.
(As an aside, I am personally shocked by the newest crop of “Data Protection consultants” I’ve seen emerging in the last few months who haven’t taken basic steps to ensure that their websites comply with the entry-level basics appropriate organisational and technical controls to protect data, like using SSL. Caveat emptor!)
Don’t, what ever you do, Click that Link!!!